How the AWS integrations work with VMware Cloud on AWS (VMC)? It is easy to understand layout (at a high level) of the VMware Cloud on AWS environment. One of the benefits of using VMware Cloud on AWS is the tight integration with AWS Services.
What I mean by this is that, as you can see in the picture above, VMware Cloud on AWS is running within the AWS Global Infrastructure, sitting next to the AWS services. This brings up an intriguing new way of thinking about how you design and leverage AWS services and the VMware stack. Some demos I’ve shown off at conferences such as VMworld and AWS re:Invent include integrations such as:
- VMware front-end and RDS backend
- VMware back-end and EC2 front-end
- AWS Application Load Balancer (ALB) with private VMware apache servers
- Lambda, Simple Queueing Service (SQS), Simple Notification Service (SNS), S3, Route53, Cognito, Alexa and more.
And these are just what the time has allowed to implement! There are many different services that you can integrate into your environment. So let’s go ahead and jump right in.
How Is This Possible?
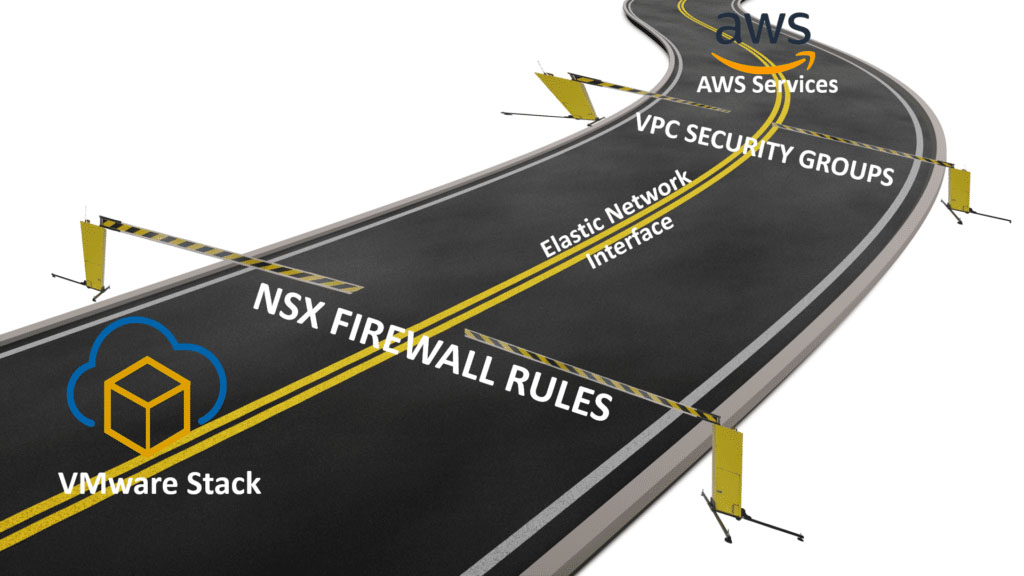
In addition to sitting within the AWS Infrastructure, there is an Elastic Network Interface (ENI) connecting VMware Cloud on AWS and the customers Virtual Private Cloud (VPC), providing a high-bandwidth, low latency connection between the VPC and the SDDC. This is where the traffic flows between the two technologies (VMware and AWS). There are no EGRESS charges across the ENI within the same Availability Zone and there are firewalls on both ends of this connection.
How do I secure the allow specific traffic across the ENI?
One way that I like to explain this traffic is by thinking of the ENI as a road between two locations, or in this case, the VMware SDDC and the AWS services.
From the VMware side (see image below), the ENI comes into the SDDC at the Compute Gateway (NSX Edge). This means, on this end of the technology we allow and disallow traffic from the ENI with NSX Firewall rules. By default, no ENI traffic can enter the SDDC. Think of this as a security gate blocking traffic to and from AWS Services on the ENI until the rules are modified.
AWS Services
On the AWS Services side (see image below), we utilize Security Groups. For those of you who are not familiar with Security Groups, they act as a virtual firewall for different services (VPC’s, Databases, EC2 Instances, etc). This as well should be configured to disallow traffic to and from the VMware SDDC unless otherwise configured.
Cloud Kinetics’ strategic consulting experience and engineering efficiency helps companies take their business to the next level on the cloud.