By Vinay Naidu Kumar, Engineering Lead – PS, Cloud Kinetics
Every client and customer cares deeply about security. Regardless of the domain, industry or specific application, when a workload is moved to or created in AWS, security and data protection are always important components of the architectural design. To meet these critical security requirements, organizations use AWS Control Tower and Landing Zones, which enable a secure and compliant foundation for your AWS environment.
Setting up an AWS Control Tower and Landing Zone
Setting up a Control Tower and Landing Zone for your enterprise applications can help mitigate many security risks and provide a consolidated and comprehensive view of your AWS landscape. AWS Control Tower and Landing Zone thoroughly propagate the concept of “define once and use across”. This enables you to set up a well-architected, multi-account environment in hours instead of weeks or months, utilizing best practice blueprints tailored to the organization’s needs.
As a security best practice, it is always recommended to have a multi-account approach, where accounts can be categorized based on application/environment/business-unit etc. This approach enhances security through segregation and isolation of workloads and data. This will also significantly reduce the surface attack area when there is a security compromise.
As your organization and customer needs grow, you will have a bunch of accounts to handle – that is when the Control Tower and Landing Zone comes to the rescue as it provides centralized control and policy management across the accounts.
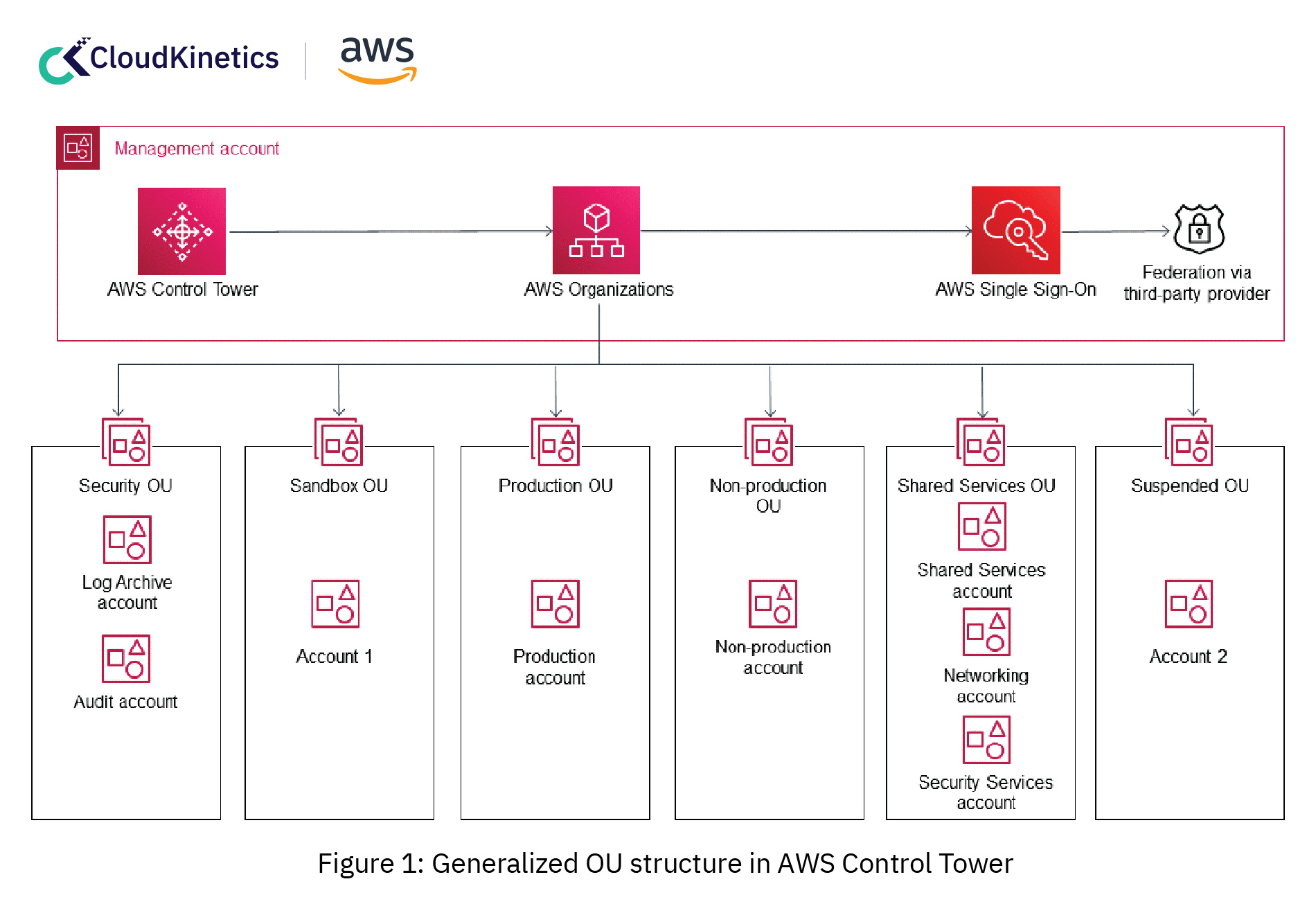
Figure 1 here depicts how you can have all AWS accounts under AWS Organizations and tap on Control Tower features to enforce security and governance.
Setting up a Landing Zone is always one of the best approaches for customer applications running on multiple AWS accounts, if you want to ensure strict traffic inspection, central security logging, and cost savings.
Building a Landing Zone with AWS Control Tower: Core concepts
Here are the core concepts at play while establishing a robust AWS Control Tower and Landing Zone foundational implementation.
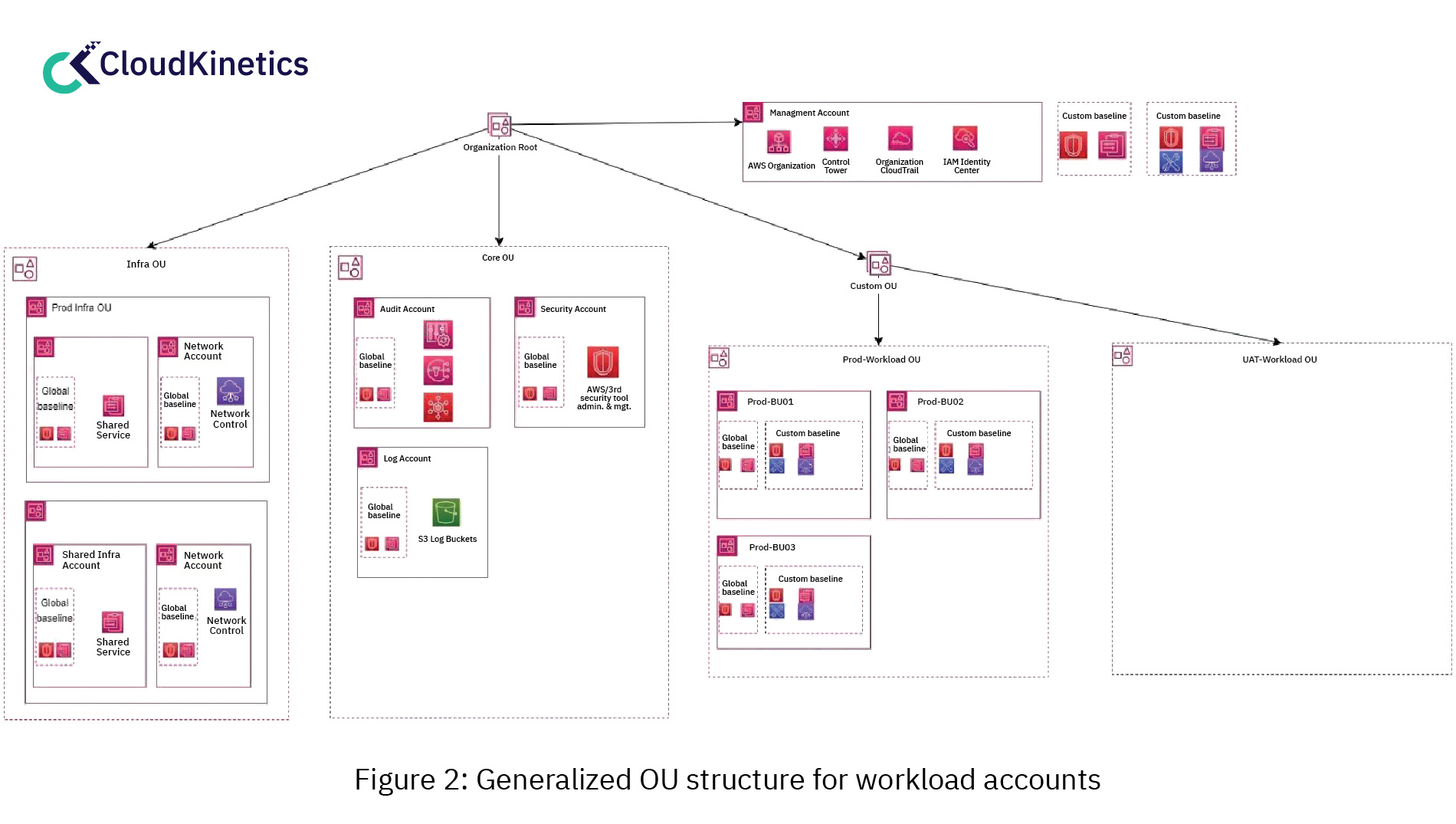
Organizational Units: When it comes to planning Organizational Units (OUs), there is no one-size-fits-all approach. It should be based on the best way you can categorize your workloads.
For example, an enterprise company with numerous applications, business units and multiple environments (e.g. Dev/UAT/Prod) can be structured as shown below.
Service Control Policies/Guardrails: Service Control Policies (SCPs) are effectively a policy-driven preventive guardrail. AWS SCPs/guardrails provide organizations with robust tools for optimizing and centrally managing governance, security & compliance enforcement, permission management and operational efficiency. These features make them critical components of a well-architected multi-account strategy in AWS. We recommend you enable all the required guardrails as per industry standards. To get started with AWS Best Practice guardrails, you can refer to the official AWS guidance documentation found here.
You could also create a Test OU within which you can enable and test the effect of guardrails without impacting any production workloads. This is prudent when teams may be unaware of how an SCP guardrail may impact your team’s day to day activities.
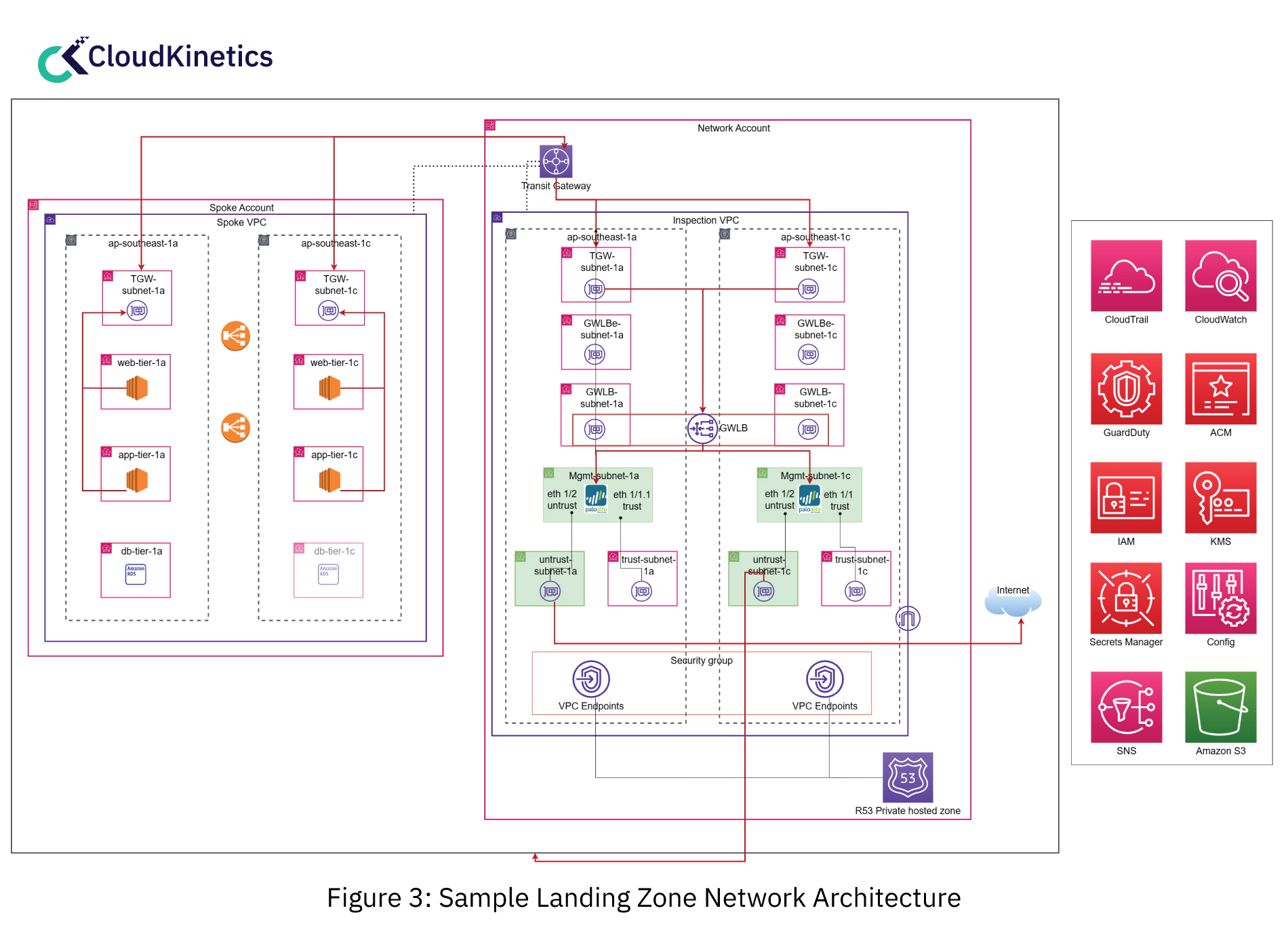
Networking for Landing Zone: This is the most important part which often consumes a lot of time for planning. We recommend that organizations should plan for three different types of traffic flow:
- Ingress traffic: The Landing Zone should have a highly available firewall for ingress traffic inspection. Organizations can choose from a number of firewall appliances in the market today, including native AWS Network Firewall.
- Egress traffic: Plan for a central NAT gateway to manage all the egress traffic originating from workload VPCs from all AWS accounts and ensure it is being inspected using the firewall. This saves cost when all your workload VPCs use a central NAT gateway instead of individual NAT gateways for VPCs and enhances security through comprehensive monitoring with a holistic view.
- Inter-VPC traffic: Also referred to as East-West traffic, this is internal traffic between the VPCs within the AWS accounts. Best practice is to have inter-VPC traffic inspected using a firewall to detect internal threats, prevent data exfiltration etc. However, you can choose to ignore inspection for some VPCs – for example, those which require high throughput and require less latency.
We recommend you further define any other flows for your workloads and analyse its effects including latency, costs when it traverses transit gateway, or other cost incurring components.
Figure 3 here shows one of the ways you can design your architecture to achieve the above-mentioned traffic inspection and flows. It uses hub and spoke architecture using AWS transit gateway.
To read more about hub and spoke architecture refer to this AWS article here.
Logging and monitoring: Logs can be considered as a critical asset in any infrastructure. There are a number of different kinds like VPC flow logs, firewall logs, DNS logs, transit gateway attachment logs, application logs, and more. AWS Control Tower offers you a way to centrally store these logs in a separate “Log Archive” account. While AWS Control Tower has the capability to implement centralized storage, the responsibility of log ingestion implementation is allocated to the organization. The logs can be further ingested to other Security Information and Event Management (SIEM) platforms for analytics.
Putting things in motion
By continuously monitoring workload performance and analysing customer feedback, organizations can effectively adjust resources and processes to align with evolving customer needs, ensuring enhanced service delivery and operational efficiency.
AWS offers native service called AWS CloudWatch, to get you started with Logging and Monitoring – refer to this official AWS documentation. This should help you understand what AWS services’ logs can be centralized, among other important notes.
To sum up, using the AWS Control Tower service will unveil a holistic view of security and governance across all AWS accounts within the organization. Setting up a Landing Zone makes it easier to have total control on all of the traffic entering and exiting your AWS accounts. This will significantly reduce the surface attack area and can efficiently create a scalable architecture and ensure security best practices.
For additional Design Consultation and Cloud Engineering support, Cloud Kinetics currently offers a refined AWS Secure Landing Zone (SLZ) implementation, available here via AWS Marketplace. You can also get in touch with us directly here.